Linux for Hackers 🐧
Linux is an essential skill for anyone interested in hacking and cybersecurity. It serves as a foundation for understanding various hacking techniques and tools. This section will delve into why Linux is crucial for hackers and how it has become a fundamental skill set in the 21st century.
The first line of many hacker training materials emphasizes that hacking is the most important skill set of the current era. This is true not just for ethical hacking but also in broader contexts like geopolitical events and criminal activities. The open-source nature of Linux offers unparalleled opportunities for hackers to explore, manipulate, and innovate.

Free Training from Juniper 🎓
One of the best ways to get started with Linux and networking skills is through free training programs. Juniper Networks offers a plethora of free educational resources, including security and networking training. By signing up through their platform, you can gain access to invaluable training and even discounted certification exams.
Using the link provided, you can access our free tools ⚙ Get Started. This initiative is a game-changer for those looking to enhance their skills without breaking the bank.

Linux Basics for Hackers 📘
Understanding the basics of Linux is vital for anyone looking to excel in hacking. Many beginners find themselves overwhelmed by the complexities of the operating system, often needing to start from scratch. Books like "Linux Basics for Hackers" cater specifically to this need, providing a concise and accessible introduction to Linux.
This book originated from the author's experiences training U.S. military personnel in hacking techniques. It emphasizes the need for foundational skills, ensuring that students are well-equipped to tackle more advanced topics. The goal was to make it succinct—under 250 pages—allowing readers to digest essential information quickly.

Why Linux is Important 🌍
Linux stands apart from other operating systems primarily due to its open-source nature. This transparency allows developers to create a multitude of hacking tools that are predominantly designed for Linux. In fact, an estimated 90-95% of hacking tools are developed specifically for Linux environments.
For beginners, this means that without a grasp of Linux, one will miss out on a wealth of tools and resources available to hackers. The lack of emphasis on Linux in certain certifications, such as the Certified Ethical Hacker (CEH), is a significant oversight for aspiring hackers. If you don't know Linux, you can hardly call yourself a hacker.
Getting Started with Linux // Using Virtual Machines 💻
For many beginners, the best way to learn Linux is through virtual machines (VMs). VMs allow users to create isolated environments where they can experiment and learn without the risk of damaging their primary operating system. This is particularly useful for practicing hacking techniques safely.
Using VMs, learners can run multiple operating systems simultaneously, such as Ubuntu and Kali Linux. This flexibility enables them to switch between different environments as needed. However, it's essential to understand the hardware requirements for running VMs effectively, especially the RAM needed to ensure smooth operation.
Latest is Not Always the Greatest 📅
When it comes to software, the latest version is not always the best option. In many cases, older versions of Linux distributions like Kali may perform better than the newest releases. This has been observed in various classes where students faced challenges with new versions while older setups worked flawlessly.
Maintaining older versions can also be beneficial. For instance, some tools may function better with earlier iterations of Kali or even BackTrack. This adaptability allows hackers to utilize the best tools available without being constrained by the latest updates.
Linux Terms to Familiarise & Examples 📚
To navigate Linux effectively, it's essential to understand some key terms. Here are a few critical concepts:
- Binaries: These are executable files that can be run, similar to what Windows users might call executables.
- Case Sensitivity: Linux is case-sensitive, meaning that "Desktop" and "desktop" are different directories.
- Directories: These are akin to folders in Windows, where files are stored.
Familiarizing yourself with these terms will make your transition to Linux smoother and allow you to grasp more complex concepts as you advance in your hacking journey.

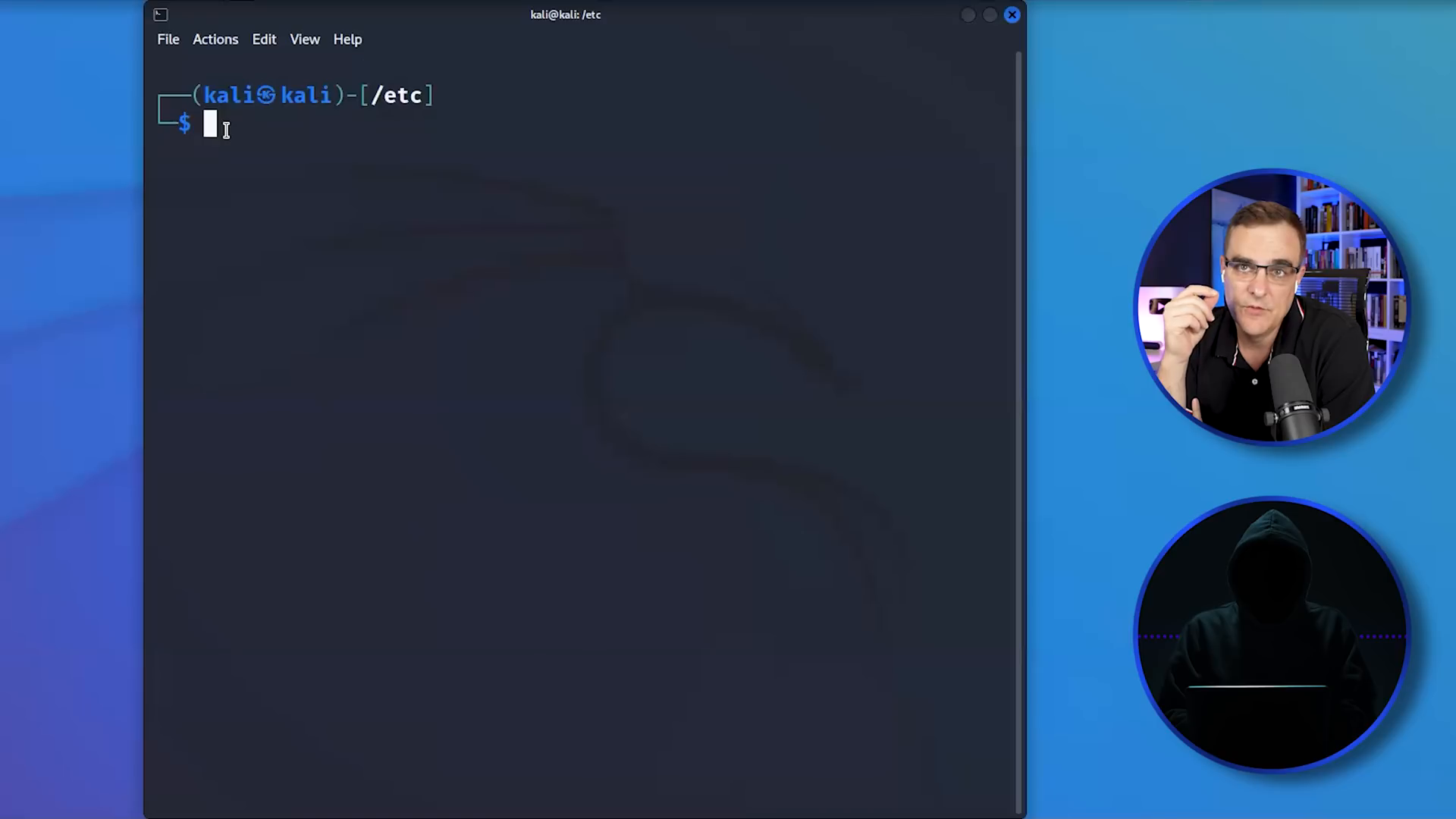
Linux File System Explained & Demo 🗂️
The Linux file system operates on a logical hierarchy, unlike Windows, which uses lettered drives. At the top of the file system is the root directory, represented by a single slash (/). Below this root directory are several important subdirectories, including:
- /etc: Contains configuration files.
- /home: Where user files are stored.
- /bin: Contains essential binary files.
- /lib: Houses library files necessary for applications.
Understanding this structure is crucial for navigating and managing files effectively in a Linux environment.

Linux Commands Demo 🖥️
Commands are the backbone of Linux operations. Here are some essential commands you should become familiar with:
- pwd: Displays the current working directory.
- ls: Lists files and directories.
- cd: Changes the directory.
- man: Displays the manual for commands.
Learning these commands will empower you to navigate the Linux environment confidently and efficiently.

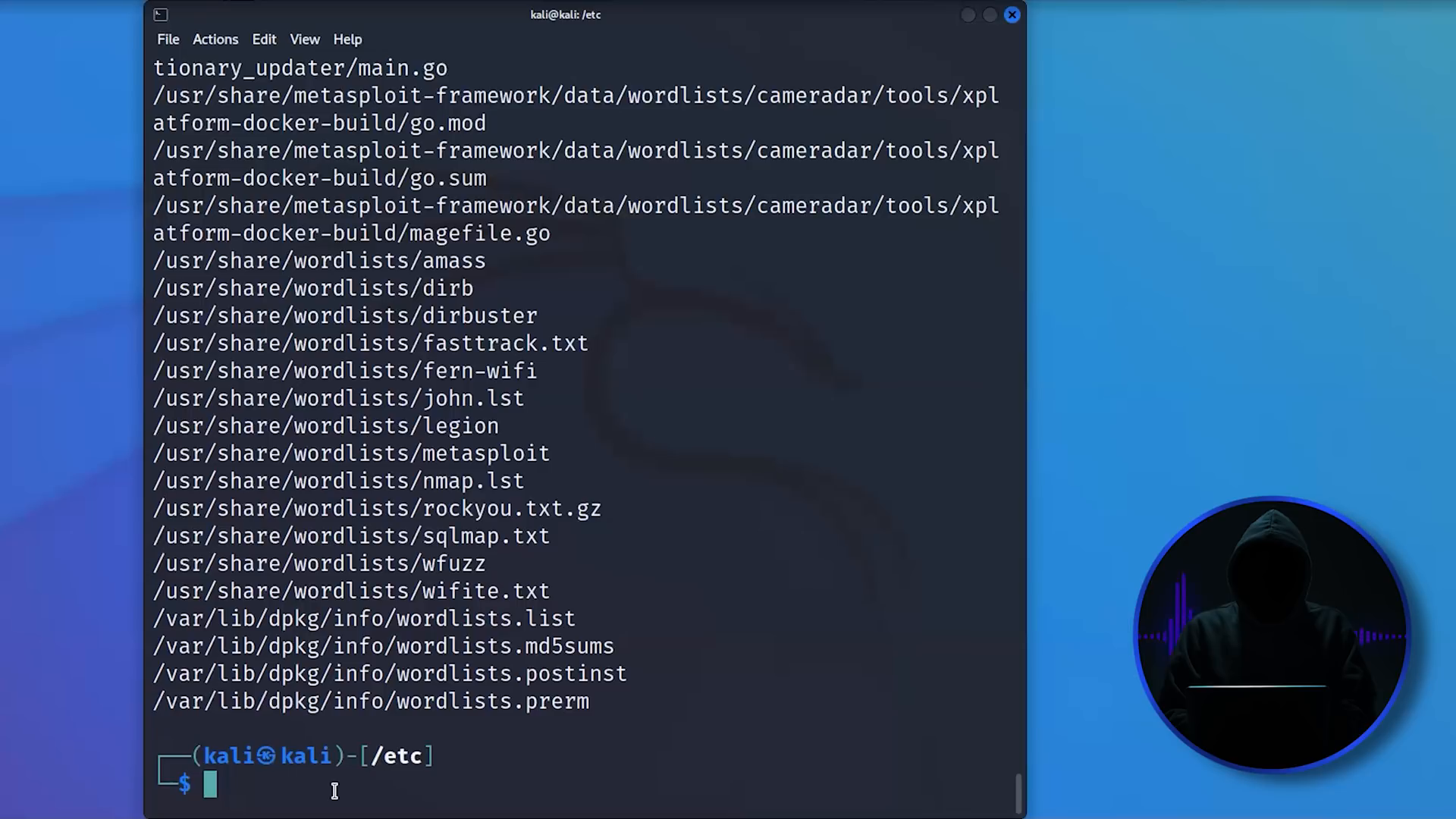
Password Lists in Linux and Where to Find Them 🔑
Password cracking is an essential skill in penetration testing. In Kali Linux, various password lists are available for use, including the famous RockYou list. However, selecting the right password list is crucial for successful attacks.
For example, the top 10,000 most common passwords can yield results more effectively than using a comprehensive list like RockYou. Moreover, considering the geographical context of your target can significantly enhance your chances of success. Using password lists in the appropriate language or context is vital for effective penetration testing.
Linux Commands Demo (Continued) 🔄
As you become more comfortable with Linux, you will discover additional commands that can significantly enhance your productivity. For instance, the grep command allows you to filter output based on specific keywords, making it easier to find relevant information within vast datasets.
Another useful command is find, which helps you locate files based on various criteria, such as name or type. Combining these commands with pipes can streamline your workflow and make navigating the command line more efficient.
Conclusion 🎉
Mastering Linux is a critical step for anyone looking to excel in hacking and cybersecurity. The skills you acquire while learning Linux will serve as a foundation for more advanced techniques and tools. With the wealth of resources available, including free training from Juniper and essential reading materials like "Linux Basics for Hackers," you have everything you need to get started.
By embracing the challenges of learning Linux, you'll unlock a world of possibilities in the realm of hacking. The journey may seem daunting at first, but with persistence and practice, you will find yourself equipped with the skills necessary to succeed in this exciting field.




